I’m very privileged to work with a range of FSI organizations across Asia Pacific (APAC) as a Regional Solutions Architect at Chef. Customers in every vertical need help and assistance with continuously auditing their environments inline with industry standards, as well as those set by governments, and independent regulators.
The Telecommunications industry is held accountable to the Signals Directorate, the Health industry is audited by HIPAA and the Financial Institutions are regulated by APRA and MAS (Monetary Authority of Singapore).
MAS is the central bank of Singapore and they publish a checklist to assist financial institutions to evaluate their controls and processes in line with the Technology Risk Management (TRM) Guidelines.
The TRM Guidelines cover 12 sections plus 5 appendices addressing a range of areas not limited to Senior Management, Risk Frameworks, IT Outsourcing, Acquisition, IT Service Management and many other areas. The items in each section include both specific and broad guideline recommendations for FSI’s dealing in Banking, Capital Markets, Insurance and Payments.
Enterprises in the Financial sector are always at risk as my colleague Galen Emery – Chef Lead Compliance Architect points out, “Automating compliance isn’t just for regulator approval. In the age of the zero-day exploit and the use of those exploits for ransomware, data leaks and other crimes against our businesses; we cannot afford to take the risk that our systems are not following best practices. And what we find in the world is the majority of exploited systems are actually due to misconfigurations and lack of best practice, resulting in compromised systems, lost business and lost consumer trust.”
Chef InSpec is used by many FSI’s in the APAC region to assist them in automating and adhering to industry best practices such as Center for Internet Security (CIS), National Institute of Standards and Technology (NIST) and Security Technical Implementation Guides (STIG). Many of the TRM Guidelines are a subset of pre-existing CIS or STIG and therefore automating them with Chef InSpec requires little effort as the heavy lifting has already been done.The MAS TRM Guidelines can easily be turned into human readable code using Chef InSpec by breaking them into a set of controls that form a profile. For example, Section 11.1.5 states, “Password controls include a change of password upon first logon, minimum password length and history, password complexity as well as maximum validity period.” In Chef InSpec this is represented as:
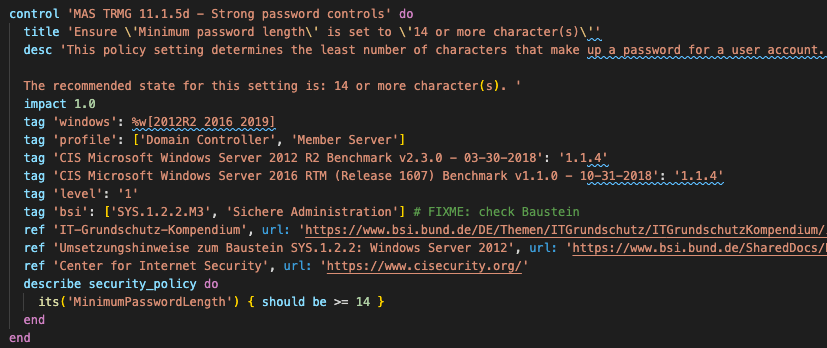
These MAS TRM guidelines represented as Chef InSpec code can now be executed continuously against an FSI’s technology platforms to ensure compliance. Should modifications be required, the code can be changed, checked into source control and tested through a continuous integration and delivery pipeline. Chef InSpec also allows the mapping of MAS TRM guidelines to CIS benchmarks using a simple tag syntax, allowing organizations to compare their audit standards to industry best practices.
Reporting is simple as the Chef Automate dashboard allows for users to access scan results. User access is governed by Identity and Access Management, giving granular control and restricting visibility where necessary.
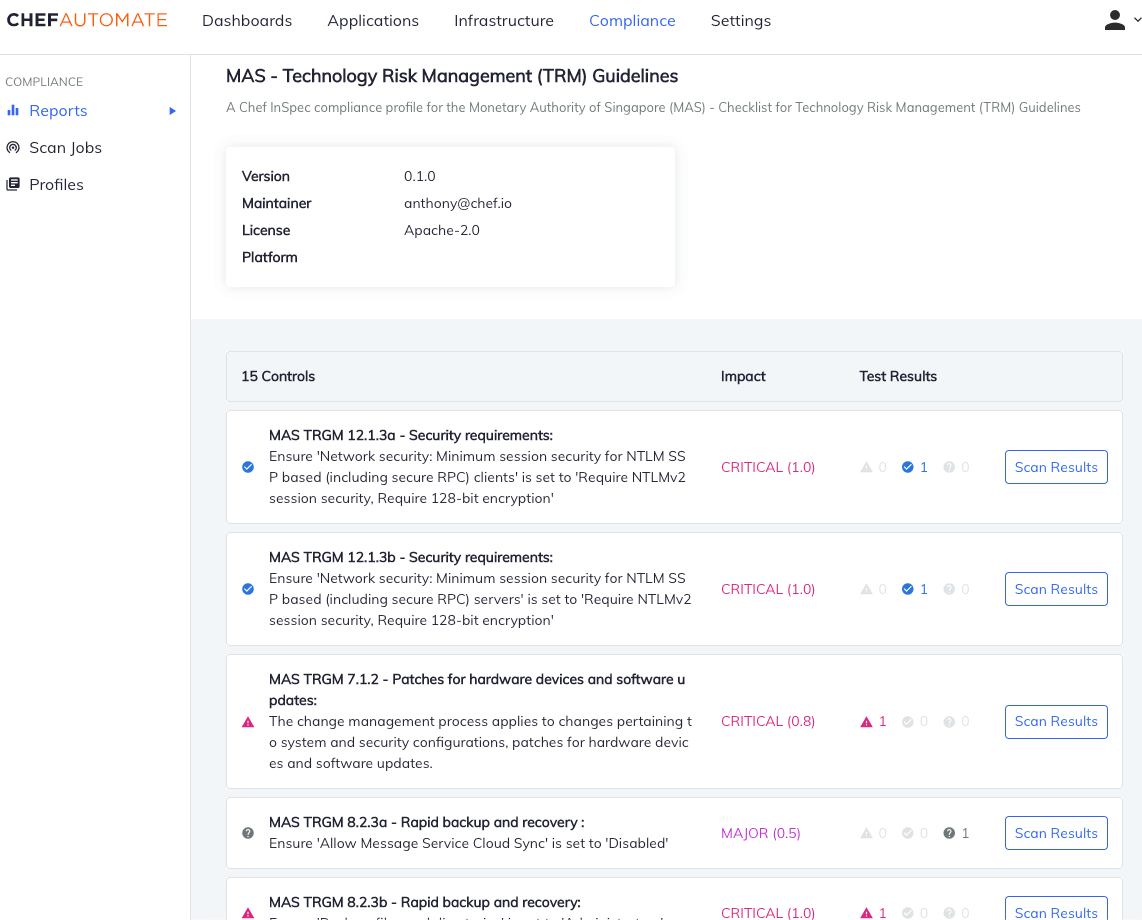
Chef also has the ability to remediate issues identified by the MAS TRM guidelines. Remediation is performed by Chef Infra using cookbooks which simply specify the policy that should be applied to the technology platform to ensure it meets the TRM guidelines.Chef has a dedicated team based in Singapore who can help your organization automate to meet its compliance requirements, whether they be for the Monetary Authority of Singapore or any other regulator. You can contact the Chef Singapore team here – asean@chef.io.

