Overview
As your applications grow and become more complex, so can your worries about the risks to your environments and ensuring they comply with your system polices and regulatory standards. While administrator deal with audits and other routine work, they also need to work on planned projects.
DevSecOps teams could manage their endpoints with existing tools for small fleets of devices, but challenges arise when you begin to scale. This is where Chef InSpec comes into the picture.
About InSpec
Chef InSpec is a security and compliance testing tool that can help you address these concerns by providing an easy-to-understand (human-readable) and customizable code framework. InSpec helps define expectations for the systems you manage and detect any deviation from your set policies. It’s easy to get started because InSpec does not require an agent to work with Linux, Windows or macOS target nodes to scan and verify configurations.
It also provides a great amount of flexibility in how you go about that detection process. For ad hoc point-in-time scans, the InSpec command-line utility allows you to evaluate any system reachable over SSH or WinRM. InSpec can also be used with Chef Automate to scan thousands of nodes at once in on-prem, cloud, and edge environments.
InSpec DSL
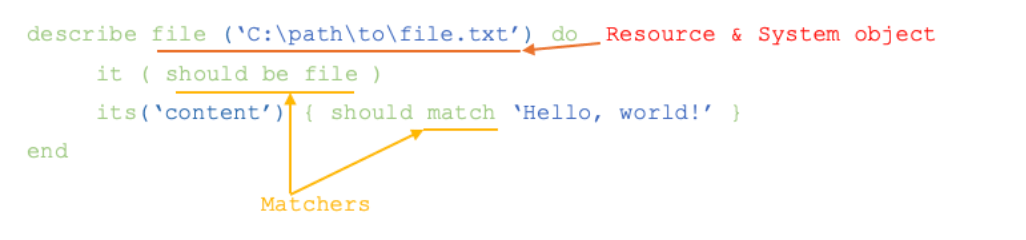
InSpec Tests
The following example tells InSpec to look at a specific file on a target node and confirms that it contains “Hello, world!”:
Setting up your Environment
Install Chef Workstation
The best way to get started with InSpec is to install Chef Workstation, a collection of tools that enable you to create, test and run Chef code.
You can install Chef Workstation by downloading an OS-specific installer for Windows, Linux or macOS.
How to detect installed software using InSpec
A Profile Example
Chef has built-in generators to create profiles and other Chef content, including cookbooks, files, and templates. For InSpec, a simple command generates a profile folder, a controls sub-directory that holds the actual InSpec code, and an
inspec.yml file that contains metadata about your profile, including its name and version.
Run the following command to generate a profile:
$ inspec init profile profile-name
$ inspec init profile auditd
The inspec.yml file contains the title, maintainer, copyright name, copyright email, and summary of the profile. This information provides metadata used to identify the InSpec profile, helping you to keep track of different profiles and versions when using both the command line and Chef Automate, the graphical Chef dashboard.
name: auditd
title: Ensure auditd is installed
maintainer: Akshay
copyright: Akshay
copyright_email: akshay@example.com
license: Apache-2.0
summary: An InSpec Compliance Profile to check auditd
When you run the inspec command, it caches all the dependencies needed for your tests and stores them in an auto-generated " inspec.lock" file.
Example of a Control:
control 'file-test' do
impact 1.0
title 'Test for file'
desc 'Check if the file is created'
describe file '/home/ec2-user/newfile.txt' do
it {should be_file}
end
End
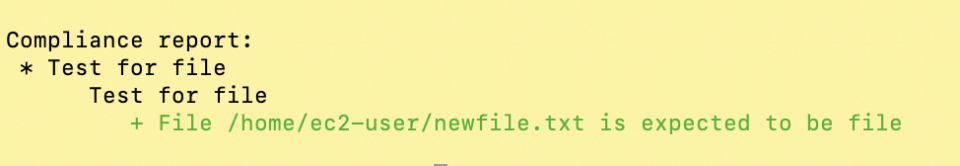
If all the given criteria are met, you'll see results in the terminal or in the Automate UI.
In addition to tests, every control includes its impact weighted value from 0.0 to 1.0 to describe its criticality. Most InSpec profiles consist of many controls, which allow you to categorize results as minor (0.0 - 0.3), major (0.4 - 0.6), or critical (0.7 - 1.0). Controls also contain titles and descriptions to help you and your teams understand what the profile is doing. You can also add tags for even more searchable metadata.
InSpec works over SSH and WinRM scanning Linux, Windows system, and macOS. No Chef Infra client agent is required on your target systems, but you should have SSH users and passwords set up to interact with Linux and macOS systems. Windows systems must have WinRM enabled with permission granted to an authorized user.
Using the InSpec code on a target node
You can run ad hoc Chef InSpec profiles against any target node reachable by your workstation. You can also set up Scan Jobs in Chef Automate to run profiles against hundreds or thousands of nodes all at once.
To run a simple ad hoc scan from your workstation, use the following syntax:
$ inspec exec /path/to/profile -t ssh://user@target –i
/path/to/id_rsa
To target Windows, use the following syntax:
$ inspec exec /path/to/profile -t winrm://target --user < username > -
-password < password >
Windows requires the WinRM-authorized user and password.
Using Chef Supermarket – Community Profiles
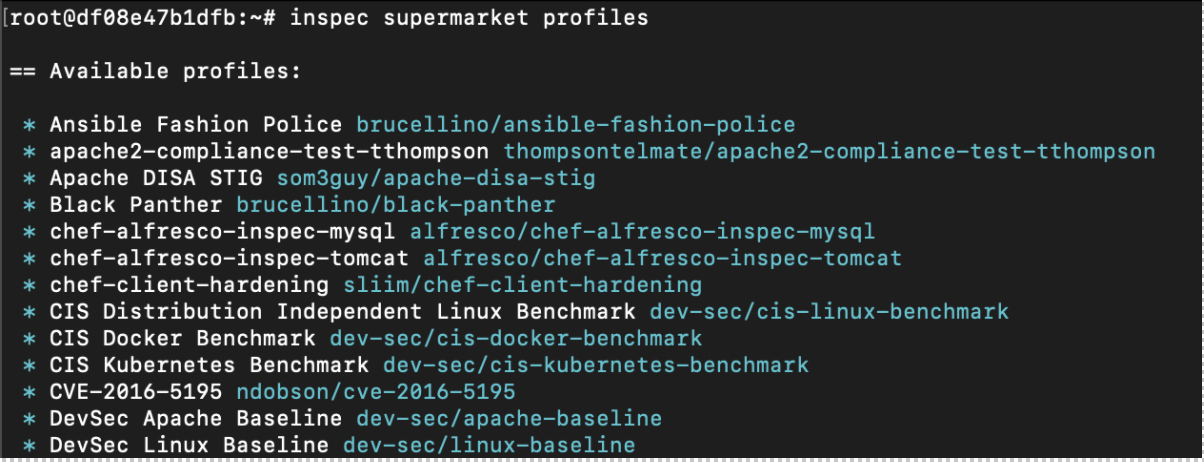
In the above example, you used a custom profile you created, but you can also run publicly available profiles using the Chef Supermarket. You can list available profiles with a simple command:
$ inspec supermarket profiles
This simple command queries the Chef Supermarket, located at https://supermarket.chef.io.
You can use the code from the Chef Supermarket to check for multiple scenarios, such as verifying a package has been installed on Linux OS (Operating Systems), log data has been written to disk, a percentage of disk space is available, and more. You can use these profiles without having to manually download them. Just use the following command, which applies the dev-sec/linux-baseline to your target node and shows you the results:
$ inspec supermarket exec dev-sec/linux-baseline –t
ssh://user@target –i ~/.ssh/id_rsa
Using profiles available in GitHub
$ inspec exec https://github.com/dev-sec/linux-baseline.git -t
ssh://user@target –i ~/.ssh/id_rsa
Automate Scan Jobs
For example, if you want to use a CIS (Center for Internet Security) security benchmark for Ubuntu, just search for the OS, select the profile you want, and click the Get button to download that profile to your Automate server, where it can be used for your node scans.
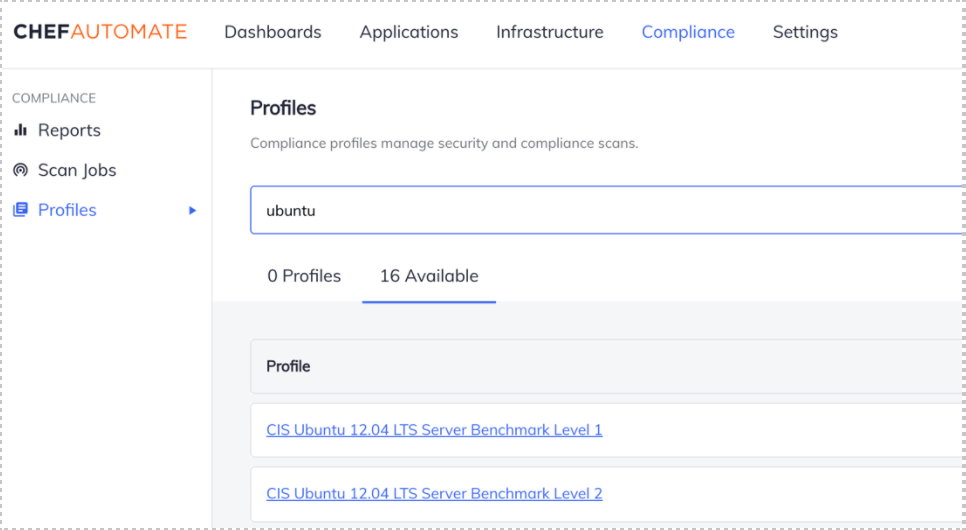
Scan jobs created in Chef Automate can be set to run once or on a schedule, enabling you to confirm node compliance over time without any human interaction.
A few InSpec Code Examples
control 'port-check' do impact 1.0 title 'Server: Configure the service port' desc 'Always specify which port the SSH server should listen.' ref 'NSA-RH6-STIG - Section 3.5.2.1', url: 'https://www.nsa.gov/ia/_files/os/redhat/rhel5-guide-i731.pdf' describe sshd_config do its('port') {should cmp 443} end end
control 'Test Windows Super User' do impact 0.5 title 'Superuser Test' desc 'Make sure the Administrator user exists.' only_if do os.windows? end describe user('Administrator') do it {should exist} end end
control 'Test Super User' do impact 0.5 title 'Superuser Test' desc 'Make sure the root user exists.' only_if do os.redhat?||os.debian?||os.linux?||os.darwin?||os.bsd? end describe user('root') do it {should exist} end end
control 'Aws_Root'
impact 1.0
title 'Verify AWS user and Region'
describe aws_user (name: 'root_user') do
it {should be_admin}
it {region should be in north virginia}
end
end
control 'CHECK github.com' do impact 0.7 title 'Verify github.com`s SSL certificate' describe ssl_certificate(host: 'github.com', port: 443) do. it {should exist} it {should be_trusted} it ('ssl_error') {should eq nil} its('signature_algorithm') {should eq 'sha256WithRSAEncryption'} its('hash_algorithm') {should cmp /SHA (256|384|512)/} its('issuer_organization') {should be_in ['Amazon', 'COMODO CA Limited']}
its('expiration_days') {should be > 30} end end
#Verify the SSL certificate using a full path control 'CHECK cert using path' do impact 0.9 title 'Verify SSL certificate from a path' describe file('/etc/httpd/ssl/cert.crt') do it {should exist} end describe ssl_certificate(path: '/etc/httpd/ssl/cert.crt') do it {should exist} end end
# Verify the SSL certificate of the InSpec target control 'CHECK github.com' do impact 0.7 title 'Verify SSL certificate' describe ssl_certificate(port: 443) do it {should exist} end end
Conclusion
This document explains what Chef InSpec is and how to verify your recipes and node configurations using InSpec tests and profiles. InSpec provides a powerful way to verify the security and compliance of your systems, regardless of OS, and without any agent.
Resources
- Learn Chef is a great place to start your journey with workstation and InSpec
- Download Chef Workstation
- Watch the Chef InSpec training video

