On Friday, June 19th 2020, the Australian Prime Minister Scott Morrison called a snap press conference to reveal that the nation was under cyber-attack by a state-based actor. Following this, the nation’s infosec advice agency said that while the attacker had gained access to some systems it had not conducted “any disruptive or destructive activities within victim environments.” Australian Government and Enterprise organisations were advised to take action and be on high alert. Advice was given to ensure that systems were updated, patched and checked for common vulnerabilities and exposures.
It is a well known fact that the entry point for cyberattacks is often created by pure accident. A “well meaning” temporary change late at night to bring an application back online after an outage by opening more ports than necessary in a firewall instead of just the required one can leave a system exposed. “We will fix that in the morning and work out which one is required” is generally the justification but everyone goes to bed for some rest and the security flaw is forgotten about by the next day!
Consistency, collaboration and ‘shifting left’ your security, audit and compliance testing to ensure it is an integral part of the SDLC is the only way to solve these problems. Using code to define your information security guidelines not only gives consistency but ensures you can repeatedly test your security posture from the developer’s laptop, thorough system test and all the way into and including production.
The ACSC (Australian Cyber Security Centre) publishes the Australian Government ISM (Information Security Manual) which outlines a framework that organisations can apply to protect their systems and information, but traditionally it has been difficult to do this as it is provided in a PDF, MS Word or XML format which is not conducive to automation or converting to source code. Source code ensures benefits of version control, consistency and management of “waivers”, which are those requirements that ideally need to be implemented, but can often not be due to dependencies in the application infrastructure.
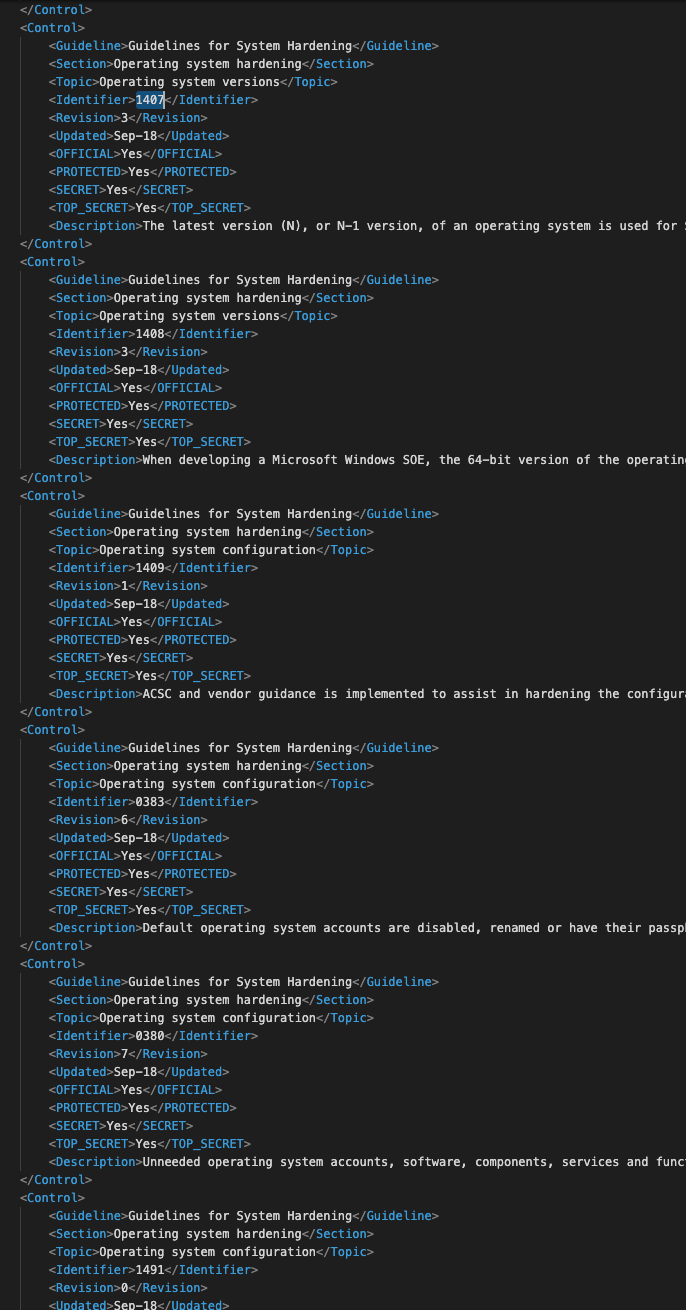
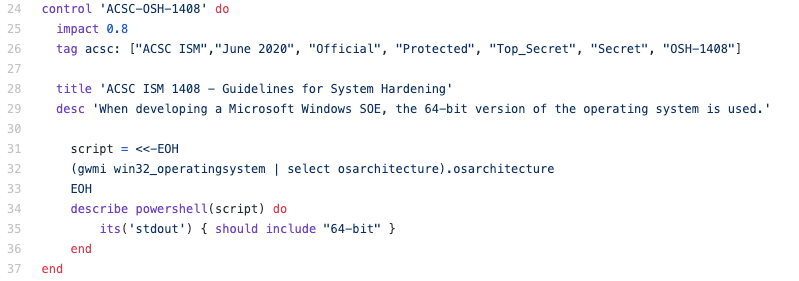
Many organisations around the world have used Chef Compliance to take defined standards like the ACSC ISM and convert it to code or simply map it to existing industry standards like CIS (Centre for Internet Security). This allows Governments, Enterprises and Schools to automate the security tests, run them continuously and turn them into code. Rather than the XML above, the Chef Compliance rules are human readable and can be shared in a code repository, plus tagged to different security levels such as Unclassified, Protected, Secret and Top Secret.
Only hours after the press conference by the Australian Prime Minister, it was announced that New South Wales school online accounts were under attack from hackers. The advisory released stated a number of known vulnerabilities in Sharepoint, Microsoft Internet Information Services (IIS) and Citrix could be exploited.
Reporting on the security compliance of Microsoft Internet Information Services, Sharepoint or the Australian Government ISM is really quite easy with Chef as there are over 400 out of the box profiles for Chef Compliance or you can simply create your own. The reports are held in time series and are searchable from the graphical user interface.
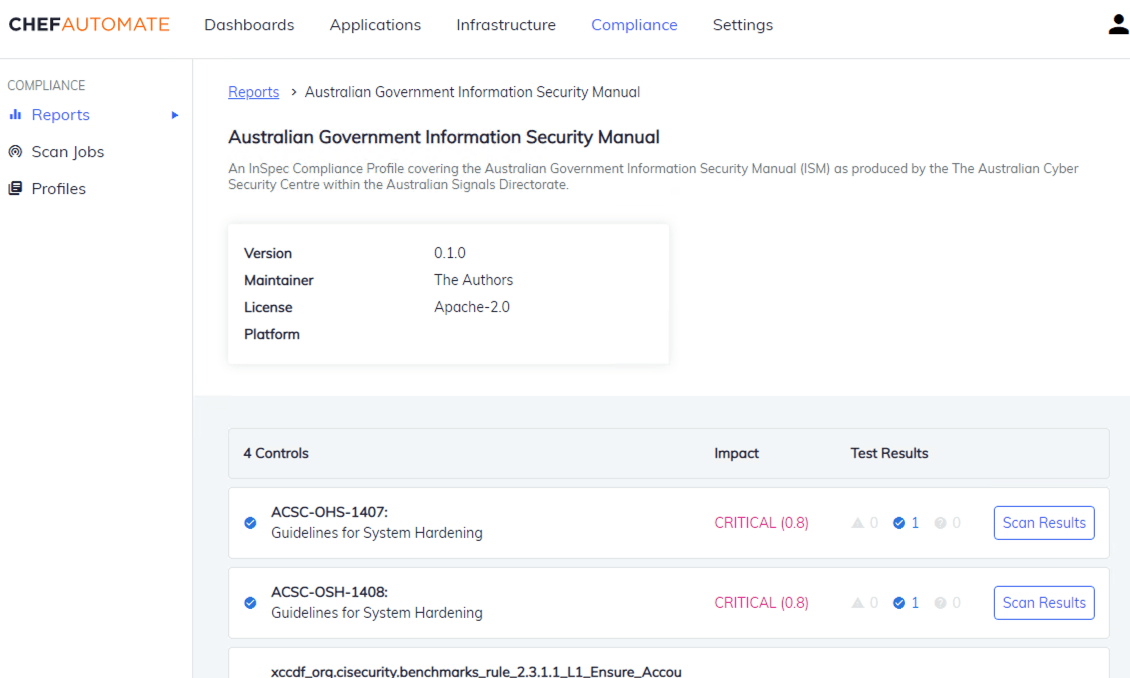
Chef also has the ability to remediate issues identified by the ACSC ISM guidelines. Remediation is performed by Chef Infra using cookbooks which simply specify the policy that should be applied to the technology platform to ensure it meets the ISM guidelines.
Chef has invested in a dedicated team based in Australia with appropriate clearance and citizenship requirements who can help your organisation to automate and meet its compliance requirements, whether they be for the Australian Government, the Monetary Authority of Singapore or any other regulator. For more details, feel free to contact me or any of the Chef Australia and New Zealand team at anz@chef.io.

