Chef InSpec is an open-source testing framework for infrastructure with human as well as machine-readable language for specifying compliance and security policy requirements. Chef InSpec compares the actual state of your system with the desired state expressed as easy-to-read and easy-to-write code. It detects violations and provides detailed reports that offers insights for remediation.
Chef InSpec has over 500 ready-to-use resources, that include AWS, Azure and GCP (Google Cloud Platform) cloud resources.
Setting up the Environment
Install Chef Workstation.
The GCP InSpec resource pack uses the native Google Cloud Platform (GCP) support in InSpec and provides the required resources to write tests for GCP.
Prerequisites:
InSpec GCP resources require a GCP client ID and secret. The easiest way to set up the credentials is via the Google SDK. Install and configure the GCP SDK by downloading the SDK and
running the installation via ./google-cloud-sdk/install.sh. Once installed, we are ready to gather the credentials:
Create credentials file:
$ gcloud auth application-default loginproject_id, type of user, etc. Which will be later populated in application_default_credentials.jsonapplication_default_credentials.jsoncat ~/.config/gcloud/application_default_credentials.json
{
"client_id": "764086051850
6qr4p6gpi6h.apps.googleusercontent.com",
"client_secret": "d-FL95Q19q7MQmFpd7hHD0Ty",
"quota_project_id": "pprdadhan",
"refresh_token": "1//0g1qk7yeYcl4JCgYIARAAGBASNwF-
L9IraCi6MyOa",
"type": "authorized_user"
}
Verify the GCP access with $inspec detect -t gcp://
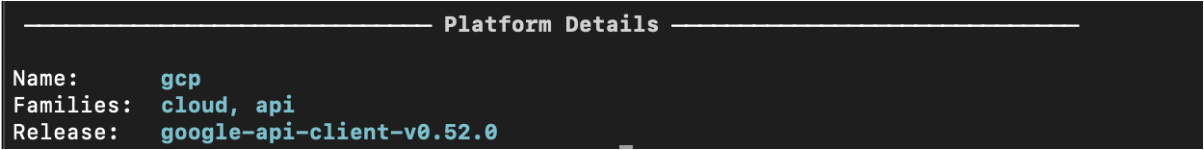
Create a new GCP profile:
$ inspec init profile gcp-example-profile
Update inspec.yml file:
name: gcp-example-profile
title: InSpec Profile
maintainer: Akshay
copyright: Akshay
copyright_email: akshay@chef.com
license: Apache-2.0
summary: An InSpec Compliance Profile
version: 0.1.0
depends:
- name: gcp-resources
url: https://github.com/inspec/inspec-
gcp/archive/master.tar.gz
supports:
platform: gcp
Edit or add a new control file based on your specific requirement.
title ‘InSpec Profile&rsquoPROJECT_NUMBER = attribute('project_number', description: 'gcp
project number')
control 'gcp-1' do
impact 0.7
title 'Check development project'
describe google_project(project: PROJECT_NUMBER) do
it { should exist }
its('name') { should eq 'ppradhan' }
its('project_number') { should cmp PROJECT_NUMBER }
its('lifecycle_state') { should eq 'ACTIVE' }
end
end
As a best practice, adding variable values in the attributes file are always a good idea.
project_number: 165434197229‘ppradhan’ exists and is in an Active state by providing project_ID as a key attribute value.
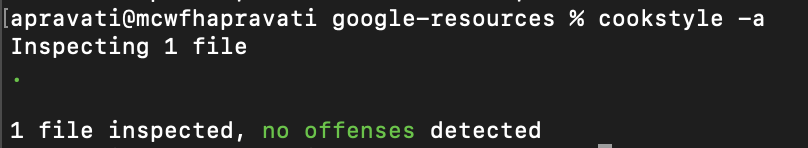
To check for any syntax error, enter the command
$ cookstyle -
To run the checks against your google account, execute your InSpec profile with google as the target provider.
inspec exec . -t gcp:// --input-file attributes.yml
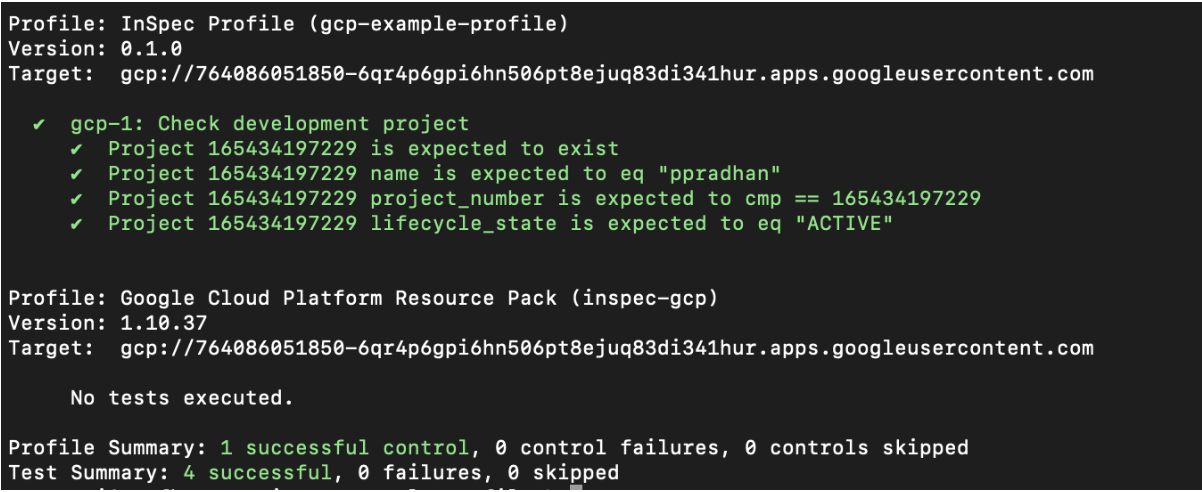
If you do not wish to use the attributes file and want to hardcode the value within the control file, use the command $inspec exec . -t gcp://

