One of the key reasons organizations look at cloud migration is to improve the security of their IT systems. Cloud vendors such as AWS bring a level of expertise and scale to security that is impossible for an IT organization to replicate in a traditional datacenter. Even so, it’s critical to understand what security tasks are handled by your cloud vendor, and which tasks are still the responsibility of the cloud customer. And as you plan your migration to the cloud, Chef can help you manage the customer-responsible tasks to detect and correct issues in your cloud infrastructure and automate the ongoing management of your security responsibilities.
AWS has created a model that defines the division of security ownership for their cloud platform. The “AWS Shared Responsibility Model” outlines how AWS commits to the security “of” their cloud, and where customers need to focus on security “in” the cloud. (see Figure 1.) Details of the Model are available in detail at https://aws.amazon.com/compliance/shared-responsibility-model/. I suggest every current and potential AWS customer spend time on this page to understand the model to help shape your migration and management strategy.
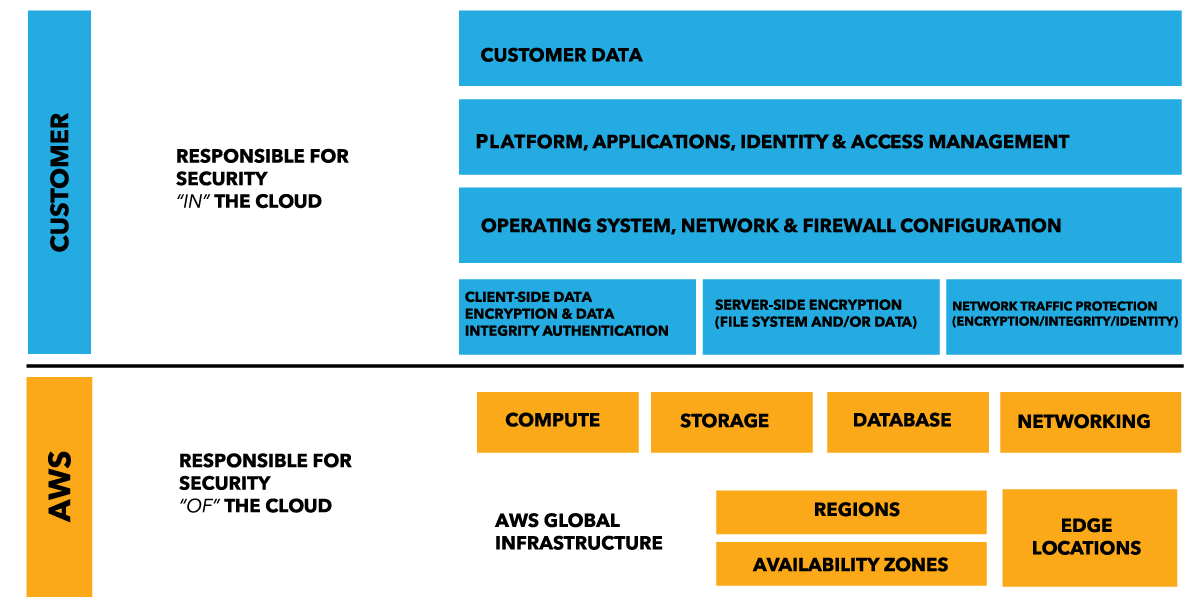
A company managing their own IT infrastructure (either bare metal or VMs) needs to create a strategy and practice to manage all of the elements in Figure 1. AWS commits to the security of their platform and distributed infrastructure as a service to their customer. While benefiting from their expertise and scale here is a huge boon for customers, it still means you need to have a plan to secure everything above the line.
AWS defines three categories of security responsibilities:
- Inherited controls: components which are fully delivered by AWS and as a result are secured by them (example, compute, storage, database and networking functions of AWS)
- Shared controls
- Customer specific infrastructure: (apps you deploy to AWS)
The good news is, for inherited controls, you can rely on AWS to supply the security of the cloud itself (and things such as physical access to servers, power availability, and other infrastructure components obviously are “taken care of” by AWS). As you move down the list, more and more security tasks fall onto customers as you focus on apps and configurations that are specific to your unique circumstances running on the AWS platform. At this level, you need to be planning how to manage the security of your instances, including user access controls (IAM), managing patches in your operating systems, which firewall ports are open/closed in your instances, and more.
Help is Here: Detecting State of Systems
As you develop a strategy for managing your role in the AWS Shared Responsibility Model, consider how Chef Automate can help you automate the ongoing management of compliance and system state in your instances by providing a means to detect and correct security issues in your systems in a programmatic, repeatable fashion. Chef provides tools to define and validate security requirements and application configurations (InSpec) and to apply configuration changes and remediate detected issues (Chef), both of which have integrations with the provisioning tools provided by AWS to allow the creation, configuration and validation of new instances all in one step. With Chef Automate, you can track and manage your full cloud estate from one place, with a fully filterable and searchable history of all audits and changes that have been performed by Chef. For AWS, Chef Automate is available as a “do it yourself” offering for existing customers running on EC2 or your own systems, through the AWS Marketplace, as well as through OpsWorks for Chef Automate, a managed service offered by AWS.
No matter how you choose to acquire Chef, it can help you fulfill your responsibilities in these ways:
- Know what’s in your apps before you migrate. Using InSpec, you can gain visibility into the state of your apps, virtual machines, and configuration settings before you migrate your workloads into AWS. Don’t ship something broken or misconfigured before you go live.
- Consistently configure new nodes and instances from a known state. Using Chef, you can define the steps required to configure an instance, and spin up new nodes against a desired state automatically, reducing the work required and enforcing consistency of the newly launched instances.
- Maintain visibility into the current state of your AWS instances at all times. Chef Automate gives you an up-to-date sense of the security and configuration state of all of your AWS assets so you can avoid configuration drift as systems evolve over time.
- Assess and validate regulatory compliance early. Chef Automate gives you access to an invaluable library of pre-written InSpec profiles based on a variety of trusted compliance frameworks to give you a head start on validating the compliance of your environments not only during formal audits, but as often as changes are being applied.
Security is one of the biggest concerns with companies migrating to the cloud. The AWS Shared Responsibility model removes the ambiguity of who is responsible for what when it comes to cloud security, and Chef helps make your part of the equation easier to manage with more consistent results.
Get the Scoop on Secure Cloud Migration
Want to learn more? Watch a recording of our recent webinar on successful cloud migrations to AWS. You’ll find details and best practices for migrating to the cloud with security in mind.

